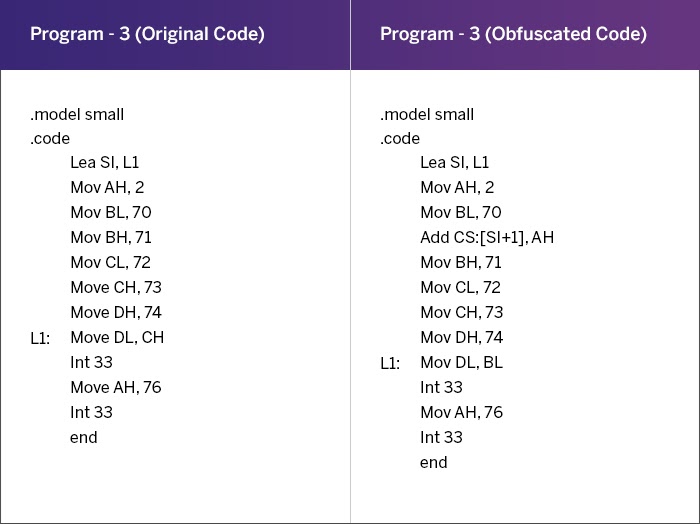
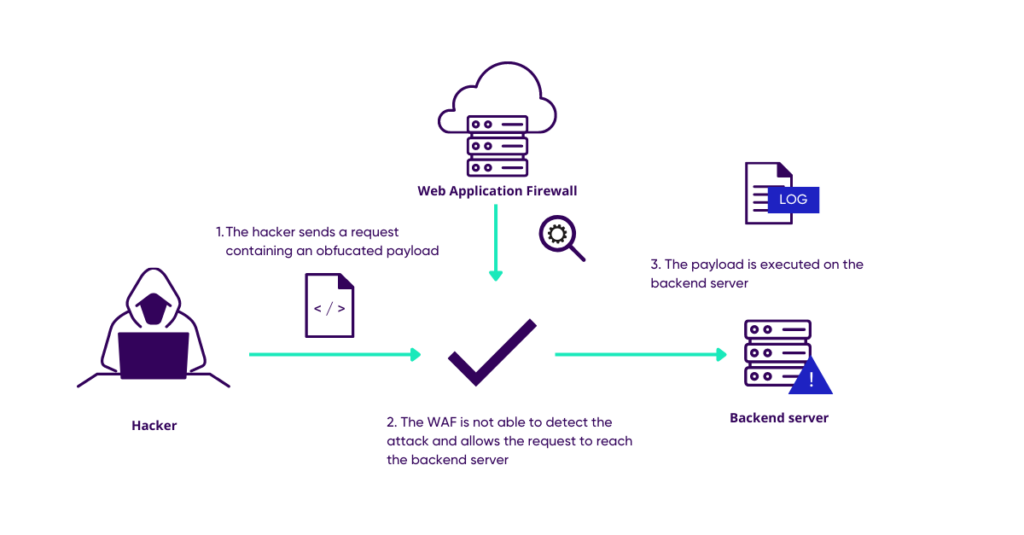
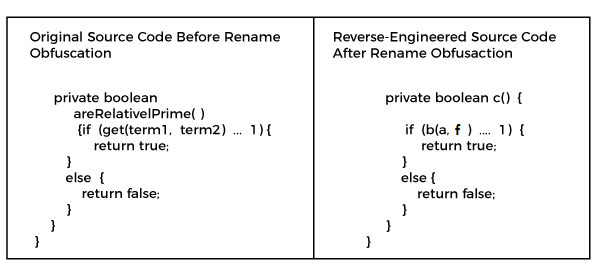
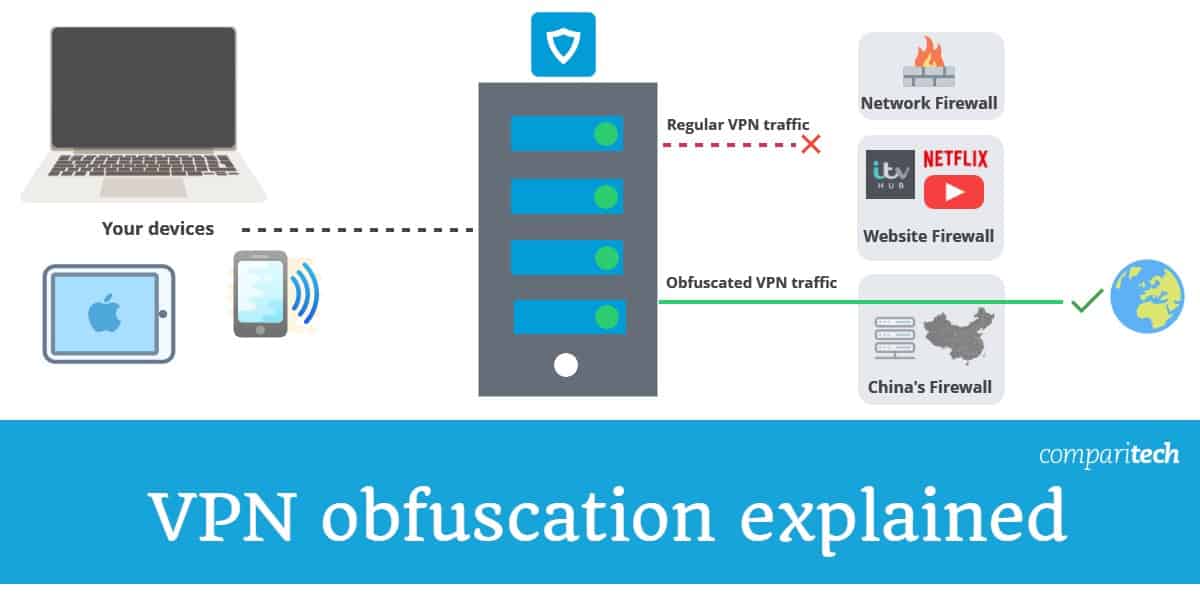
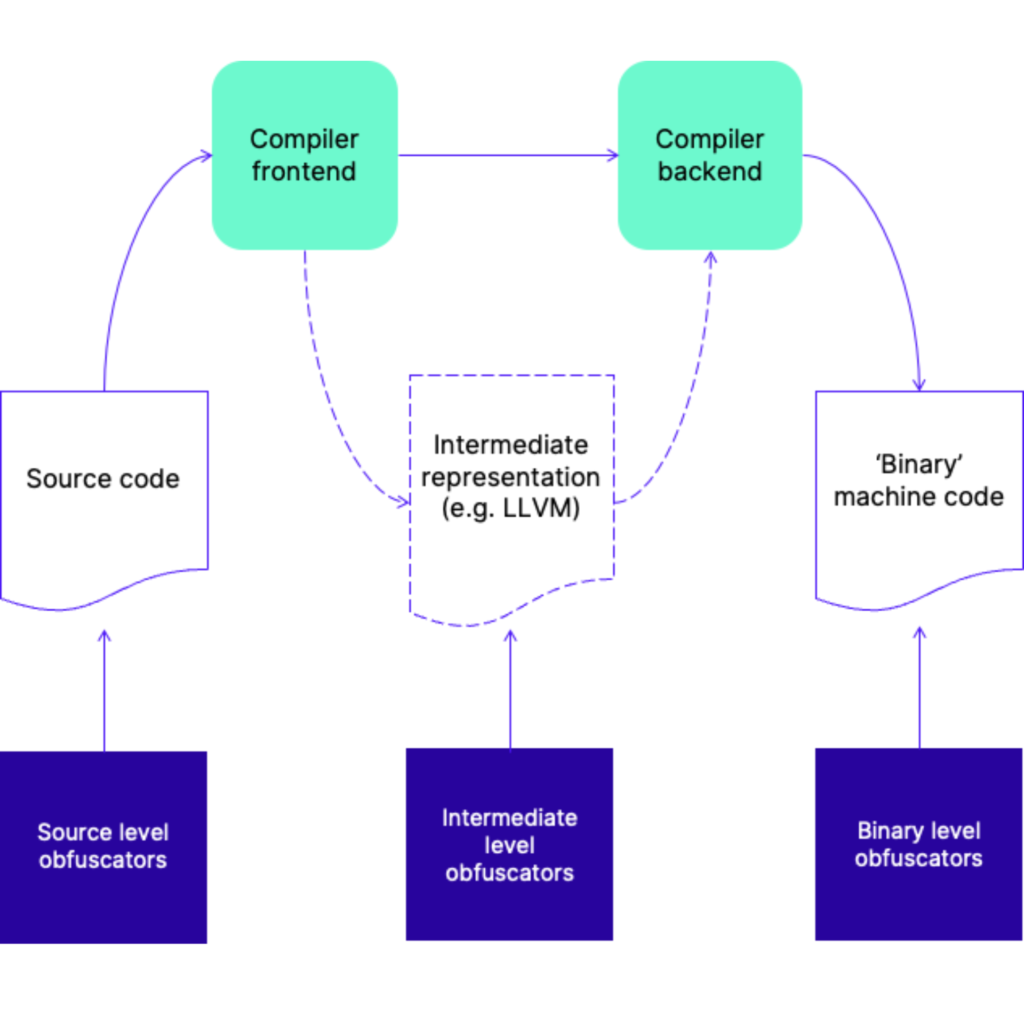
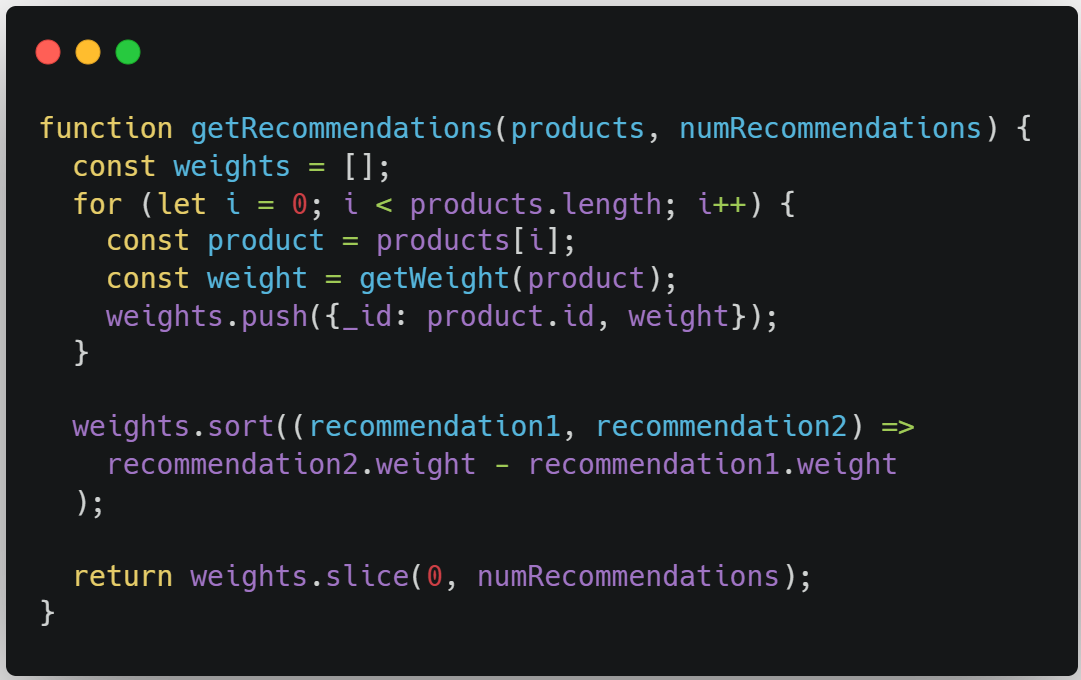
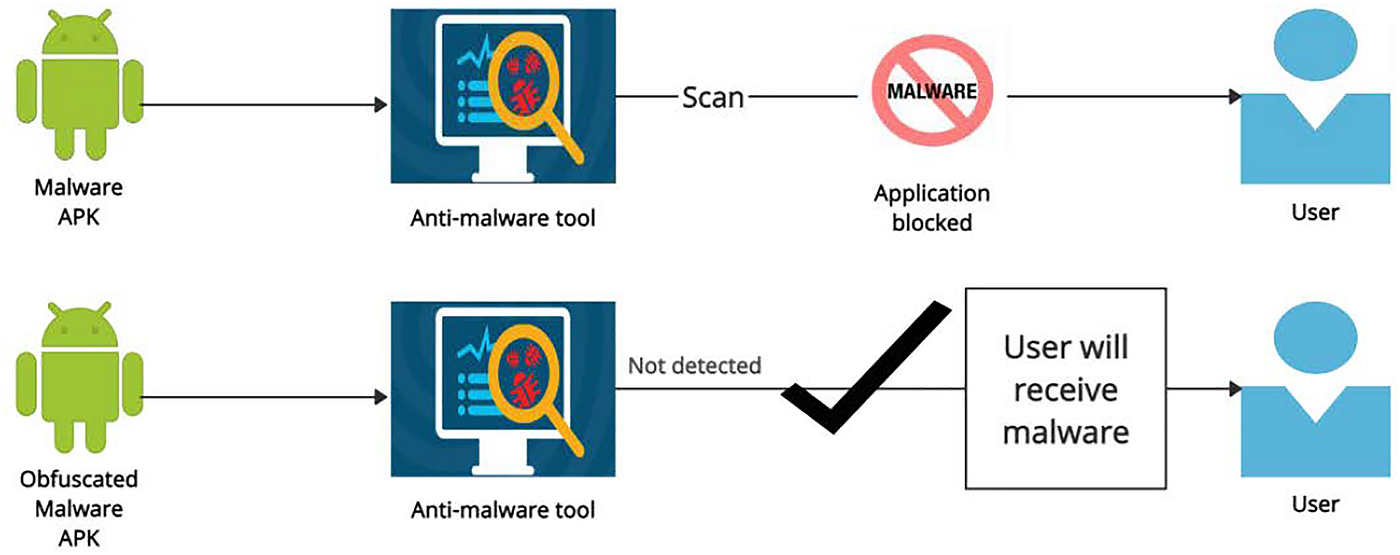
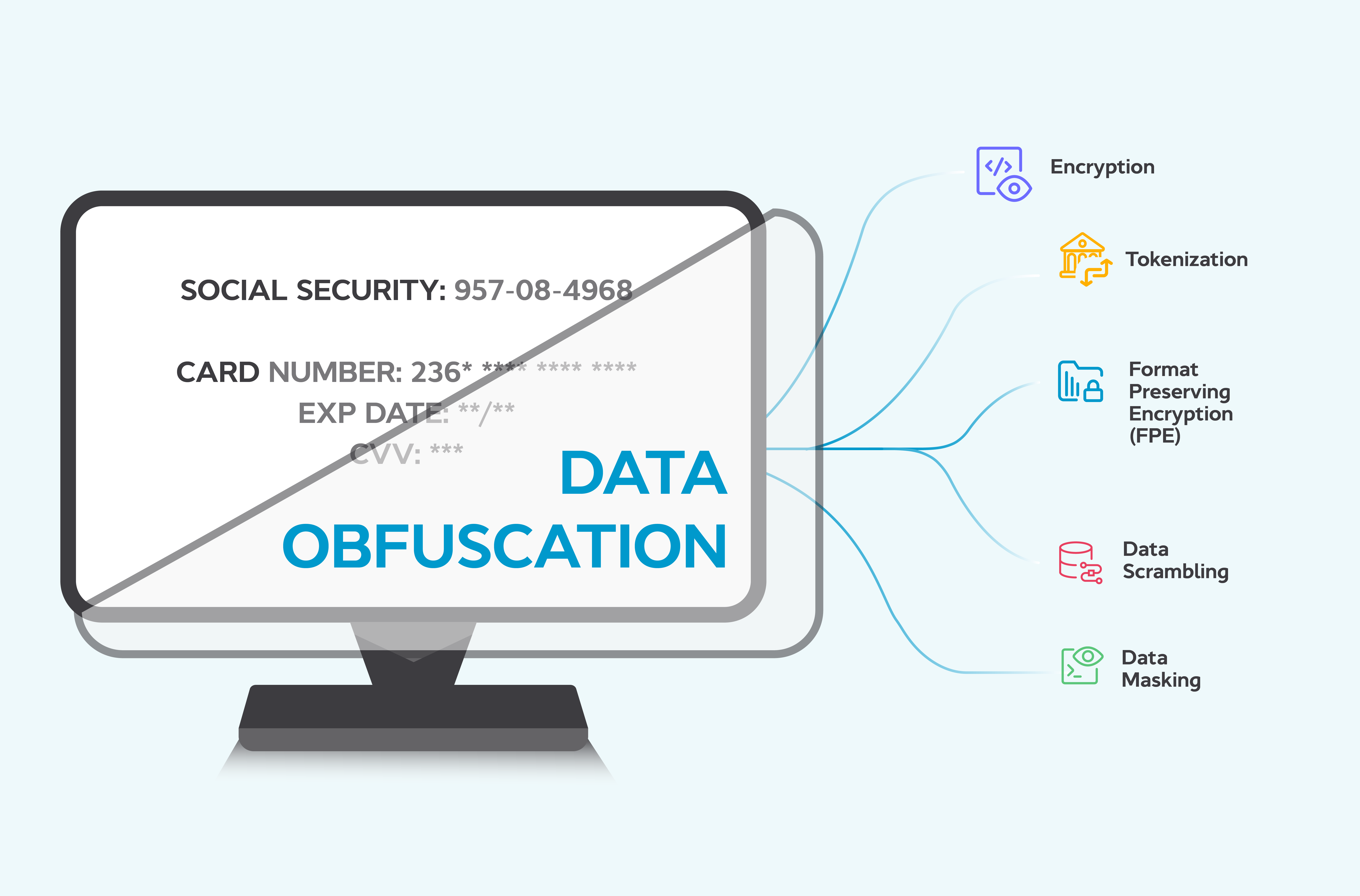
Obfuscation Techniques Ppt Powerpoint Presentation Styles Ideas Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
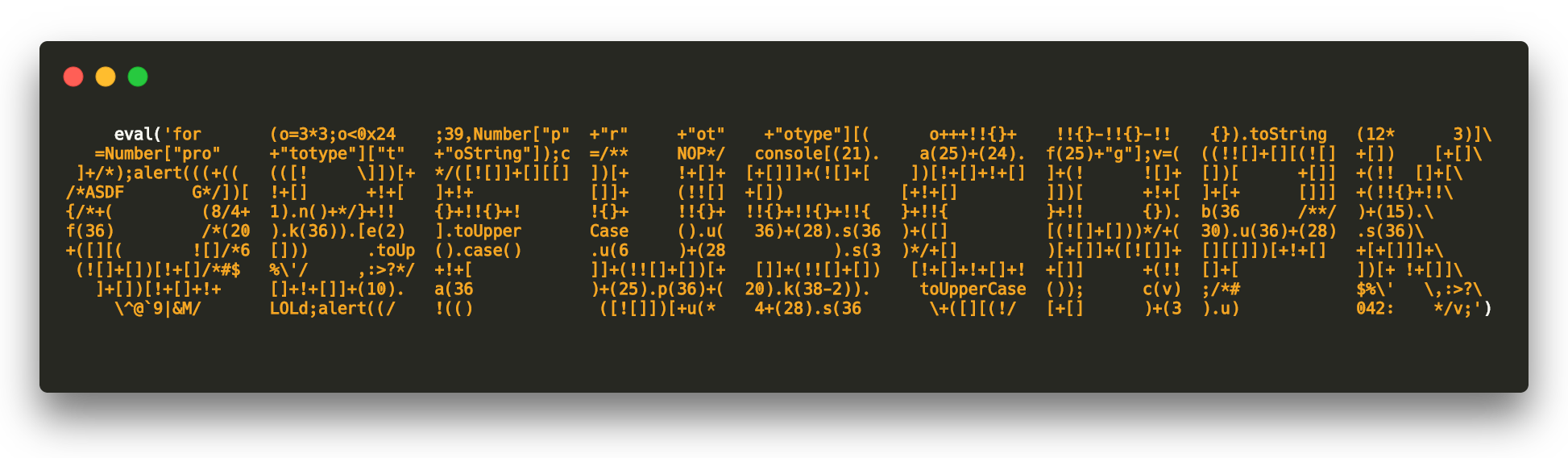
GitHub - ClaudiuGeorgiu/Obfuscapk: An automatic obfuscation tool for Android apps that works in a black-box fashion, supports advanced obfuscation features and has a modular architecture easily extensible with new techniques
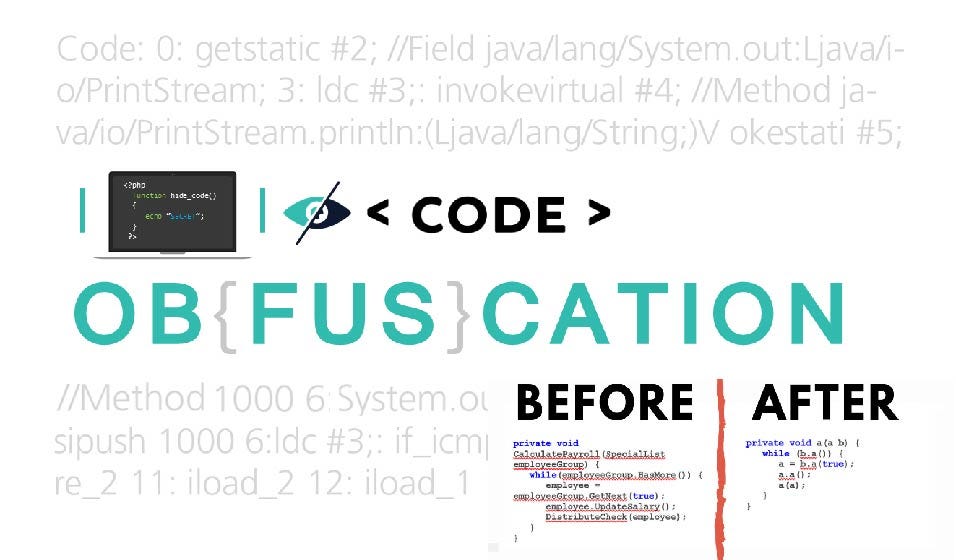
Obfuscation in Android. The process of modifying an executable… | by Supun Ishara Weerasekara | Level Up Coding