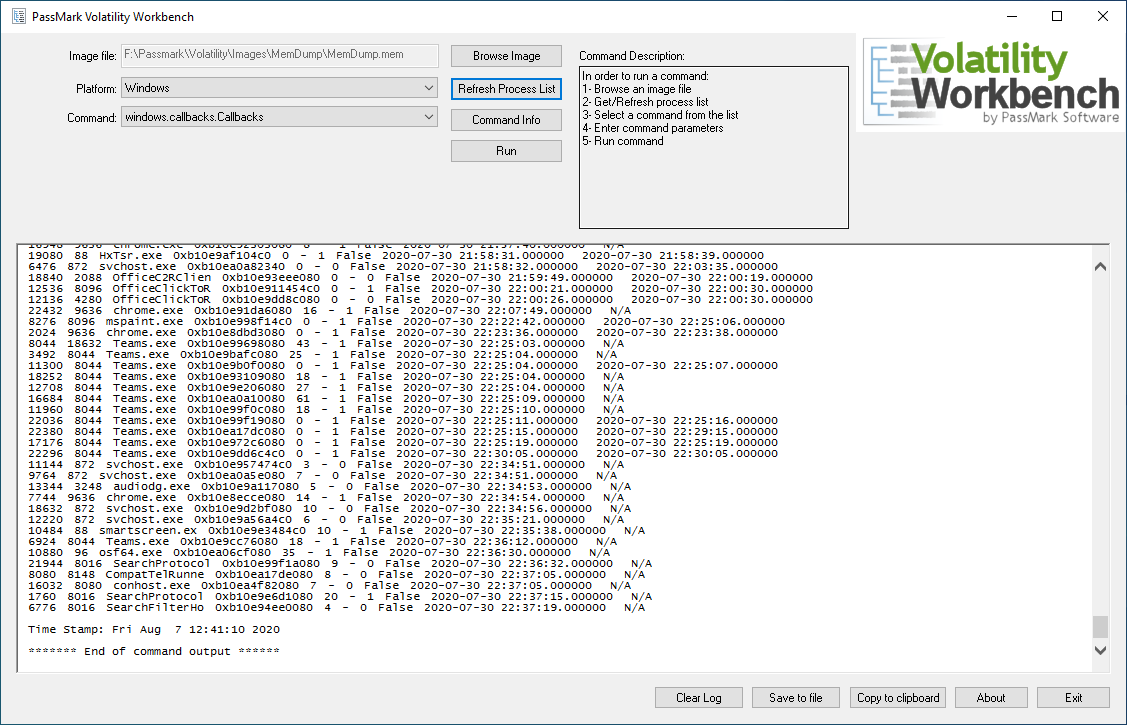
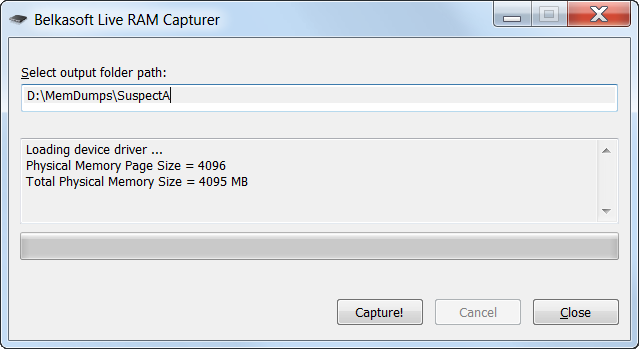
Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 14 (Live Memory Forensics) « Null Byte :: WonderHowTo
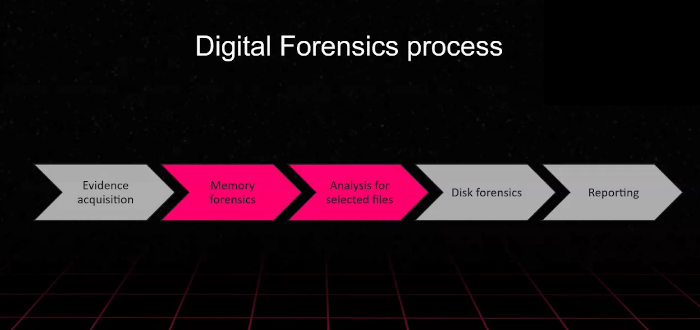
Digging up memories – a deep-dive into memory forensics in the Cyber Security Essentials meetup | Nixu Cybersecurity.

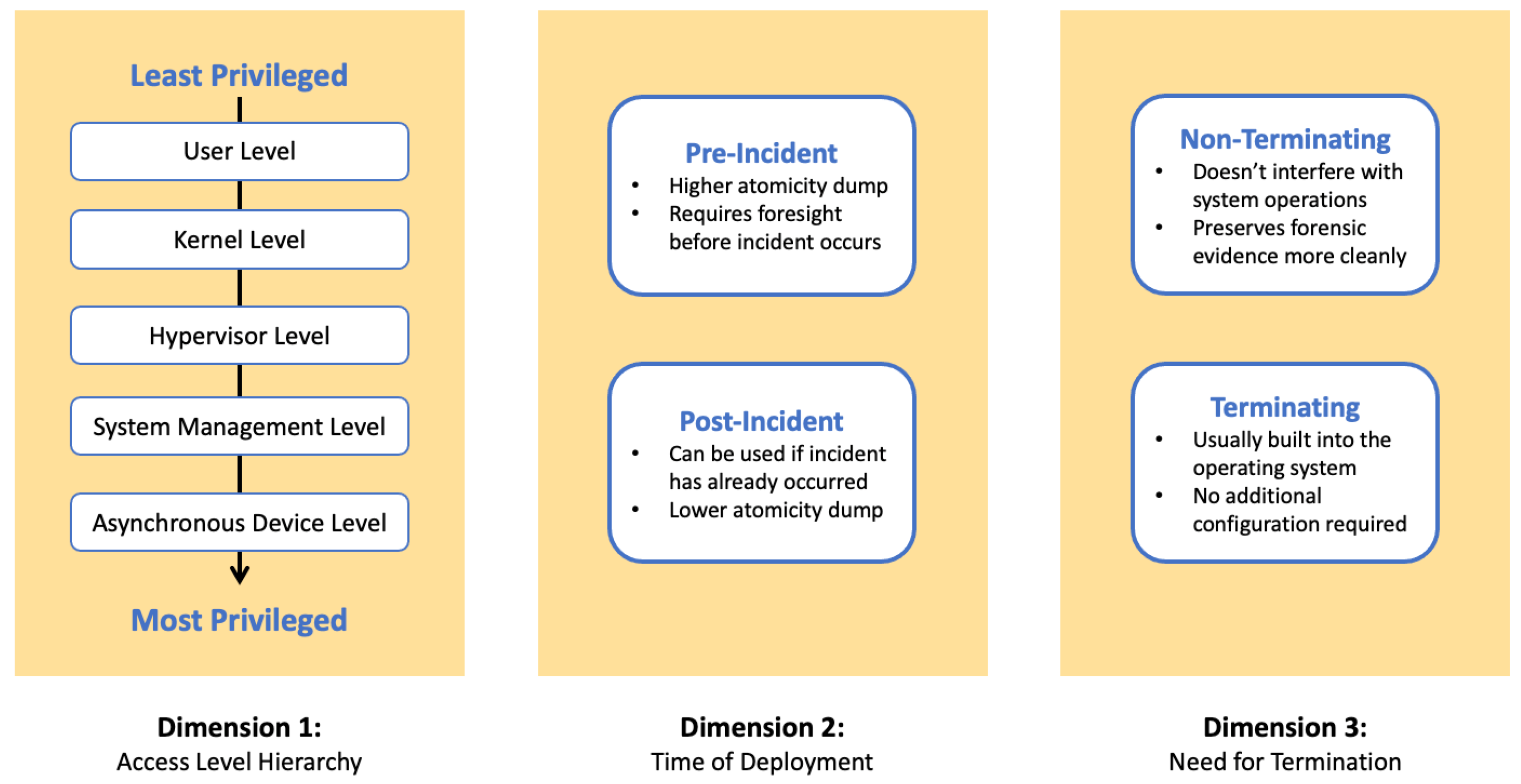
Memory forensics tools: Comparing processing time and left artifacts on volatile memory | Semantic Scholar