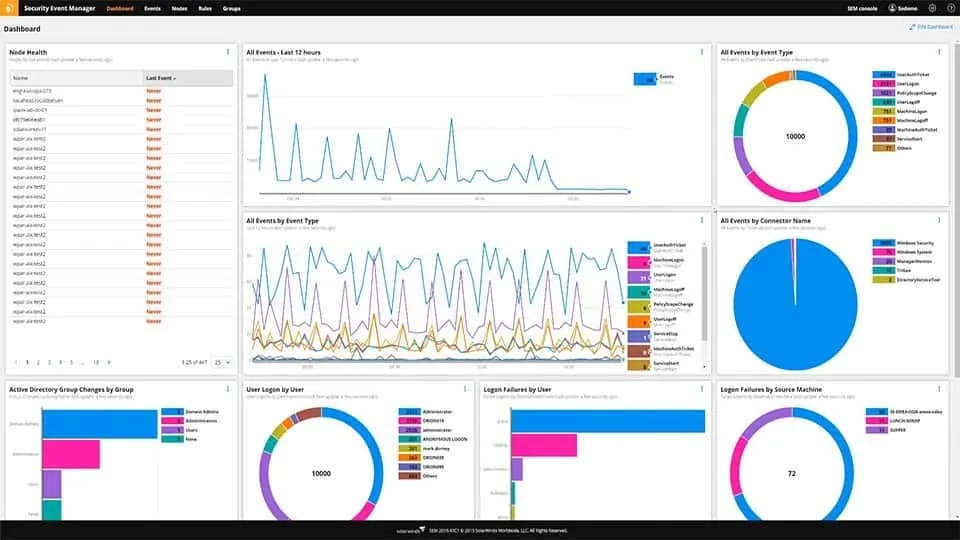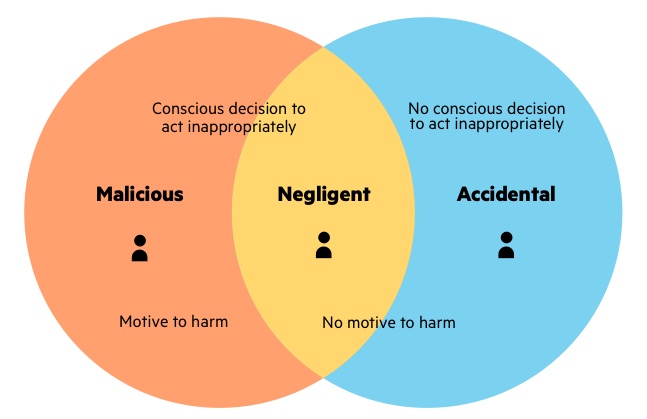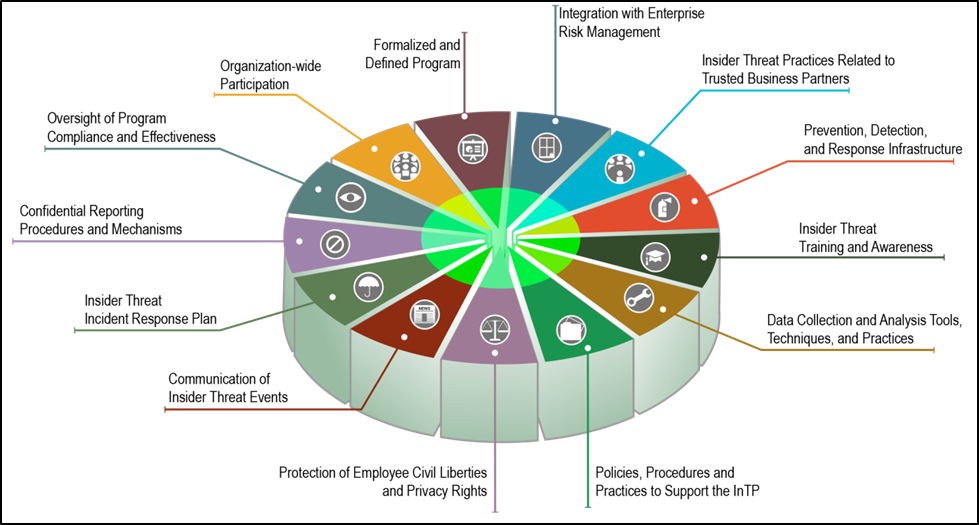
Formalized Insider Threat Program (Part 2 of 20: CERT Best Practices to Mitigate Insider Threats Series)
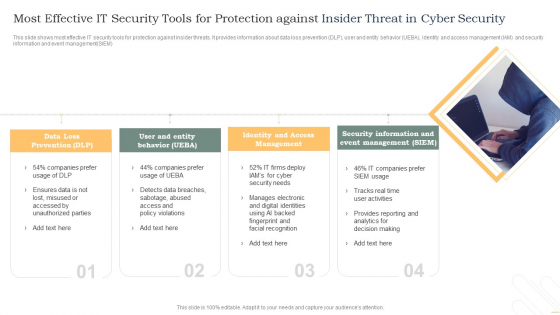
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF - PowerPoint Templates

Launching a community-driven insider threat knowledge base | by Jon Baker | MITRE-Engenuity | Medium
Insider Threat Detection Tools Ppt Powerpoint Presentation Layouts Graphic Tips Cpb | PowerPoint Slides Diagrams | Themes for PPT | Presentations Graphic Ideas

Understanding and Managing Insider Threats in Cybersecurity – Reveal Risk – Cybersecurity Consulting and Services